Poam Plan Of Action And Milestone - It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones* a document that identifies tasks needing to be accomplished. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk.
Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. Plan of action and milestones* a document that identifies tasks needing to be accomplished. It details resources required to.
It details resources required to. Plan of action and milestones* a document that identifies tasks needing to be accomplished. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones.
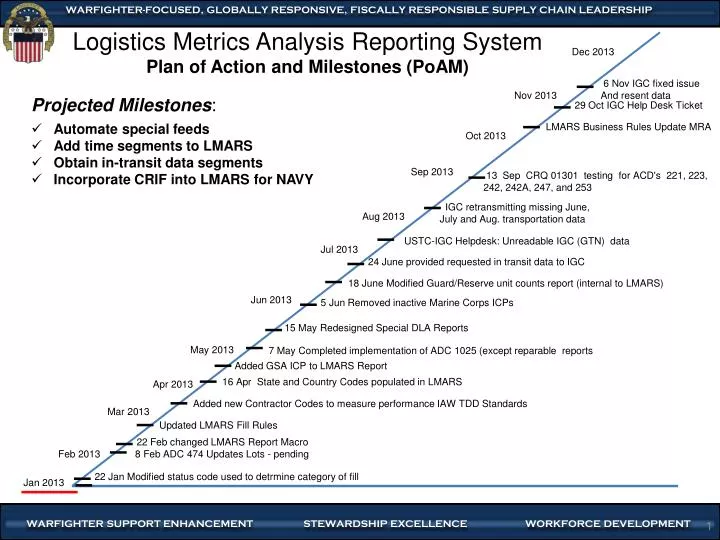
PPT Logistics Metrics Analysis Reporting System Plan of Action and
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. It details resources required to. Plan of action and milestones* a document that identifies tasks needing to be accomplished..
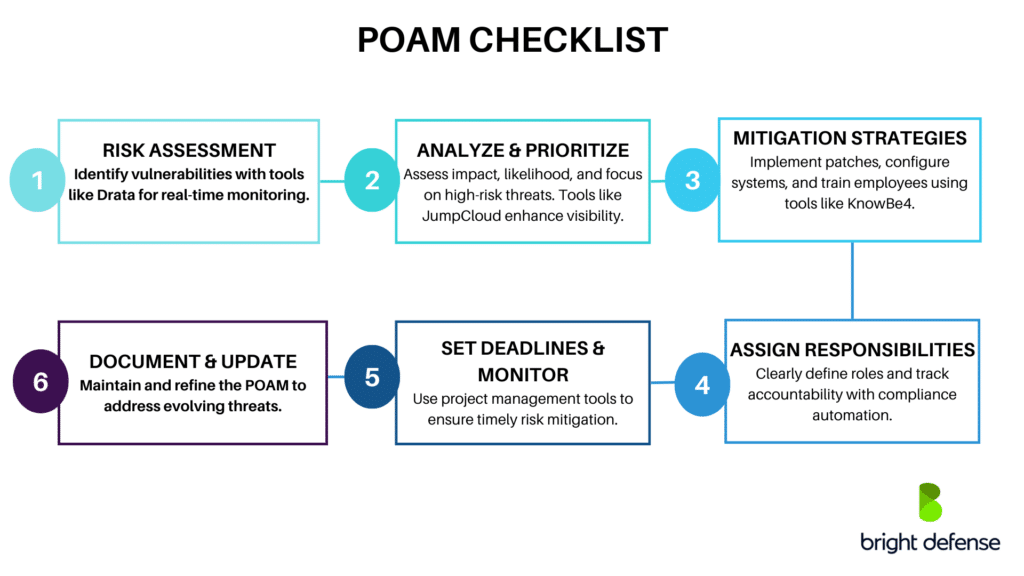
What is a POAM?
Plan of action and milestones* a document that identifies tasks needing to be accomplished. It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. This job aid is a tool to help information system security professionals understand how to create and use the plan of.
POA&M Management Plan of Action and Milestone YouTube
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system.
SOLUTION Plan Of Action And Milestones Poa M Worksheet 1 Studypool
Plan of action and milestones* a document that identifies tasks needing to be accomplished. It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. This job aid is a tool to help information system security professionals understand how to create and use the plan of.
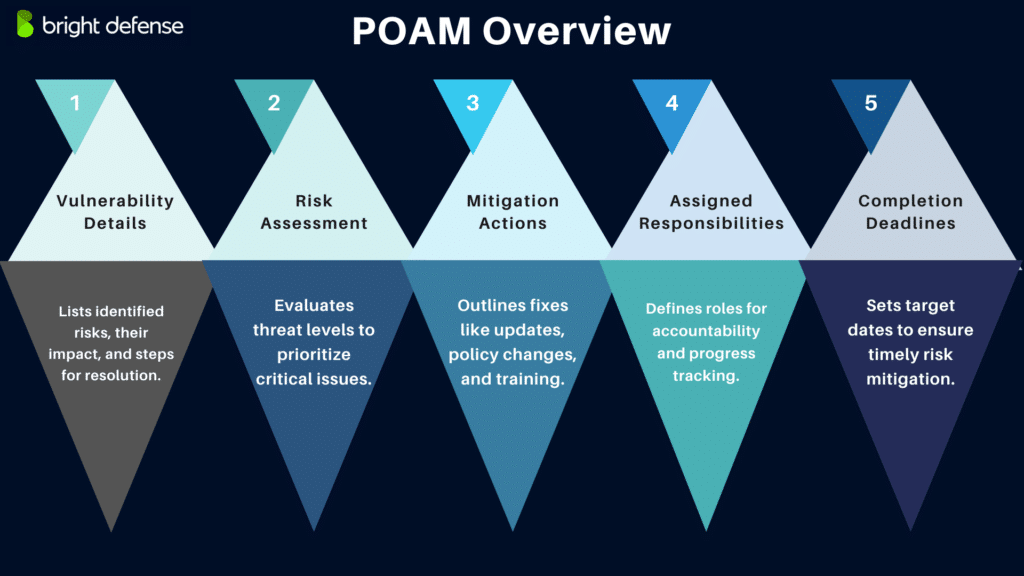
What is a POAM?
It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. Plan of action and milestones* a document that identifies tasks needing to be accomplished. This job aid is a tool to help information system security professionals understand how to create and use the plan of.
What is a POAM?
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities.
Plan of Action and Milestones (POA&M)
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity.
Plan of Action and Milestones (POA&M) for CMMC Certification Process
Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones* a document that identifies tasks needing to be accomplished. It details resources required to..
Plan of Action and Milestones (POA&M) Management Playbook OCEG
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. It details resources required to. Issos use a poa&m to identify risks to the system and track remediation activities.
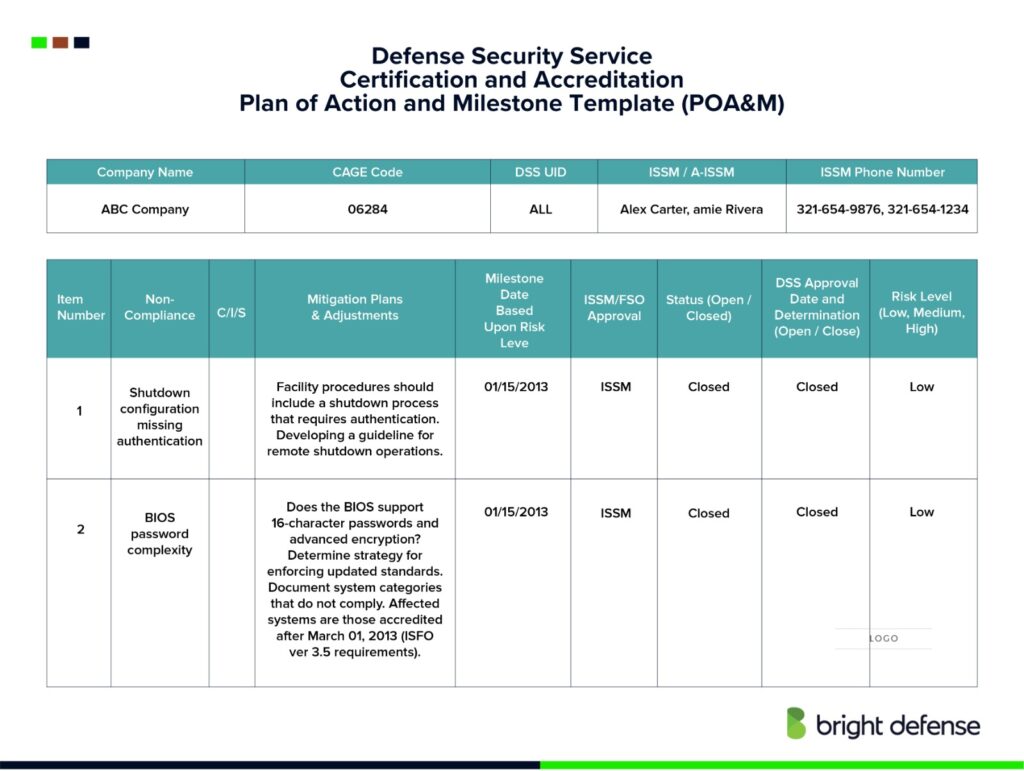
POAM NIST 800171 Plan of Action and Milestones Template
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. It details resources required to. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. Plan of action and milestones* a document that identifies tasks needing to be accomplished..
Plan Of Action And Milestones* A Document That Identifies Tasks Needing To Be Accomplished.
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. It details resources required to. Plan of action and milestones, or poam, is the corrective action component of federal agencies’ cybersecurity risk. Issos use a poa&m to identify risks to the system and track remediation activities on behalf of the system owner.